5 Risks Associated With Third-Party Vendors and How Cytellix Can Help

Many businesses work with third-party vendors in one form or another. It doesn't make financial sense to manufacture and store everything you need in-house unless you're a powerhouse enterprise. Even then, you can get high-quality products or services for less if you opt to work with third-party vendors. While there are many benefits to this type of work relationship, several risks can be involved. With the added steps involved in a vendor-business relationship, you create more opportunities for things to fall through the cracks. Risk management is key to avoid costly problems. With risk management services from Cytellix, you can protect your data, finances, productivity, and efficiency. Here are some of the top risks we protect against.
Data Accuracy and Quality
One of the risks that come with working with third party vendors is a drop in the accuracy and quality of data. As the old adage says, "if you want something done right, do it yourself." Of course, most businesses physically cannot do everything by themselves, hence why third party vendors are so popular. That being said, you have to give up some control in terms of data. The vendor is responsible for keeping track of their end of the deal, and you just have to trust them to hand over accurate data. If you want certain reports, you may or may not be able to get them depending on the data collection of the vendor company. If you are fortunate enough to gain access to the data you request, you cannot check the validity. You must trust that the vendor uses accurate processes to collect information and that they are sharing the true values with your business. Let's say you make metal widgets and rely on a third party vendor for the machining or final assembly. That vendor could say that all the parts check out and are good to go, but you really cannot validate their statement. Hopefully, your contracts allow private inspectors or auditors to confirm for you; otherwise, you could run into serious trouble. If you install these widgets into aircraft that you are manufacturing and something goes wrong, it's your contracts on the line, not the third-party vendor's. By giving up control of the data checks and quality validation, you risk someone else's mistake negatively impacting your business.
Actionability of Data
The second risk you face when working with third-party vendors is the actionability of any and all data you receive from them. Actionable data is information that can be acted upon or that gives insight into future, proactive actions. As a business owner, you know the types of data that you want to collect that will be actionable. You likely have processes in place specifically to collect, organize, and analyze this actionable data so that you can keep improving your company. When you rely on data from a third-party vendor, it may not always be actionable in a variety of ways. Firstly, as we previously discussed, unless contractually obligated, the vendor may not be required to collect any data that you require. They may have a different set of KPIs to look at, and they focus solely on those. Without the data you need, you may be limited in insights to make future plans. In terms of more immediate actions, you have even less control. A vendor is a completely separate entity that has autonomy over itself. You may notice a problem in the data, but you have no way of putting solutions in place; that's up to the vendor, and you need both contractually enabled changes or have a very flexible vendor.
Lack Of Continuous Monitoring
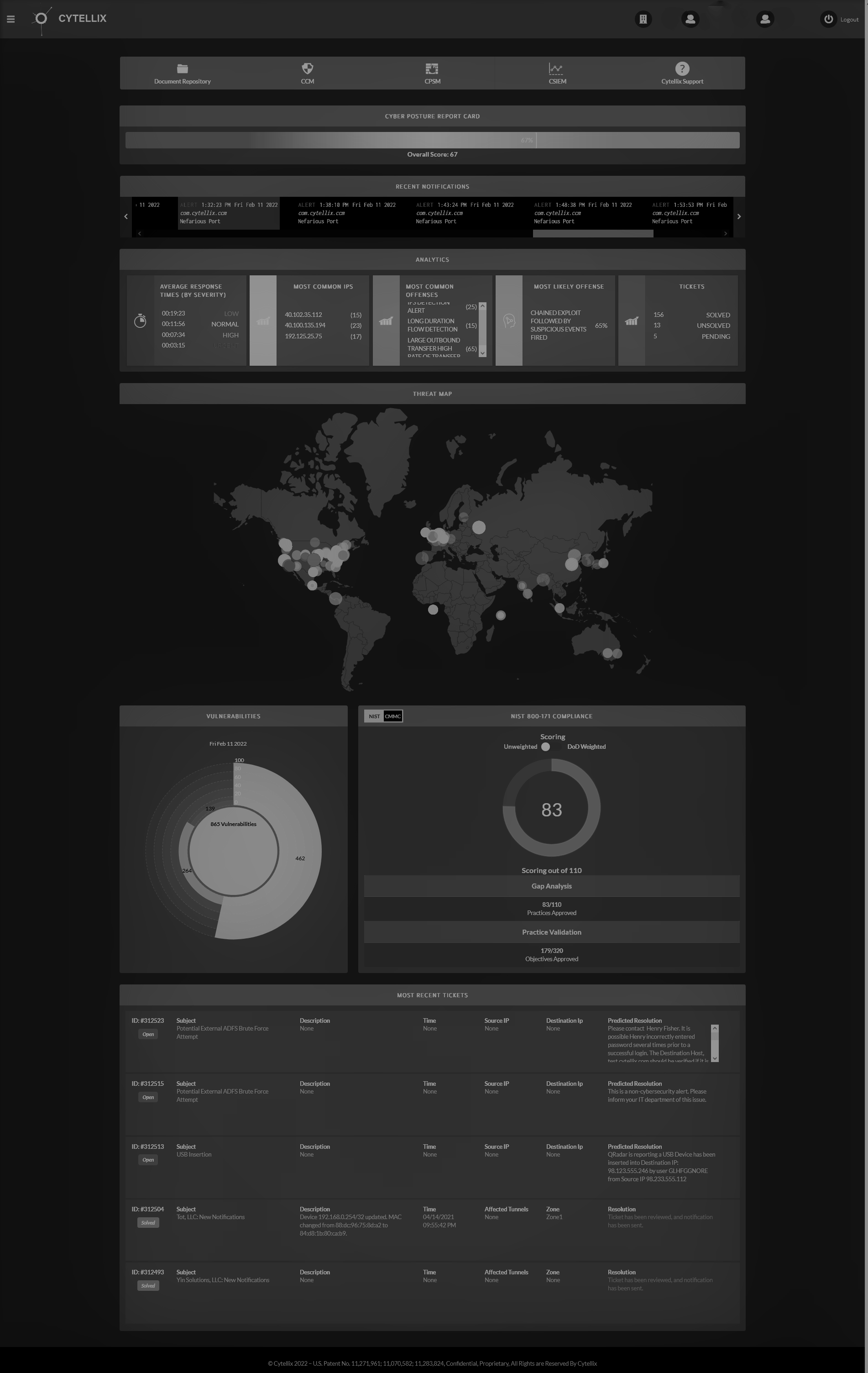
Cytellix understands how important it is to monitor all aspects of your business continuously. When you have "eyes" on all aspects all the time, you significantly reduce the risk of things falling through the cracks. The Cytellix Cyber Watch Portal was created to give clients a 360-degree view of their business’s inner workings. However, because a vendor is a separate company, continuous monitoring does not apply to them. You can continuously monitor your relationship with the vendor and any transactions taking place, but you cannot see inside their business to know anything about risk management, cybersecurity, and other things that ensure safety. Continuous monitoring is key for spotting problems before they cause chaos. We always suggest finding vendors that deploy their own measurable cybersecurity practices and continuous monitoring as you do so that you don't need to worry about the vendor electronically transferring new risk to your business.
A Slower Risk Assessment Process
We all know that processes take longer whenever there are more steps or people involved. Businesses almost always require numerous "stops" as something travels through management. Risk assessment is the same way; the more departments you have to check, the longer it takes. A vendor would add another layer to risk assessments, slowing them down and giving cybercriminals more options to attack before risks are identified and removed. Risk management is necessary to protect data and make good business decisions, and the more vendors you work with, the longer you'll have to wait for each analysis to be finished. Time is money, especially when data and sensitive information are at stake!
More Opportunities For Security Breaches
Finally, working with third party vendors can create serious risks to cybersecurity. Yes, you and the vendor work together, but you each have your own cybersecurity plan. You could have top-tier protection with all the bells and whistles, only to be breached because a cybercriminal found a way in via the vendor. A team is only as strong as the weakest link, so if the vendor is lacking in the cybersecurity field, they put you at risk by association. Hackers can break into the vendor and then find their way into your business through them. All of the safeguards you have in place will be useless if a hacker gets in from the back end. A risk management process is essential if you want to find vendors that are as security-conscious as you. We encourage you to take a look into the following cases of vendor-related security breaches from the past few years:
- Equifax, 2017- roughly 147 million users' information was leaked, including names, social security numbers, contact information, and even bank account numbers.
- Target, 2013- around 41 million payment accounts were leaked as well as personal information for roughly 70 million customers.
- General Electric, 2020 - bank account numbers, passport numbers, contact information, and other sensitive data of employees past and present were leaked.
- Instagram, 2020- thousands of Instagram accounts were compromised when passwords were leaked.
As you can see, this is an ongoing problem in the business realm that can be detrimental to companies and consumers alike. It's critical to ensure that vendors meet your standards and expectations regarding cybersecurity measures, or your business could be the next big scandal!
Cytellix has been leading the charge in the cybersecurity realm for years. We've worked with hundreds of companies to help them build their security systems, manage risks, and keep their information safe. We offer the patented Cytellix Cyber Watch Portal to offer risk management and real-time continuous monitoring 24/7. This turnkey solution is unlike any on the market and identifies risks and problems, and offers implementation of solutions on your behalf. Our state-of-the-art security measures will safeguard your company as effectively as possible while monitoring all connections for bad actors, data leakages, and user behavior changes. Even government agencies trust us to protect their most sensitive data from prying eyes. Get in contact with us
here today!

Cytellix has expert capabilities in cybersecurity technology, risk management frameworks (RMF, NIST, CMMC, GDPR, FFIEC, ISO) and provides a complete visibility platform that supports: DoD customers, DIB Customers, DoD Supply Chain, and other highly regulated industries (Finance, Automotive, Life Science, Utilities, State and Local Government). Our technology stack includes GRC, EDR, MDR, XDR, SIEM as Service, 24x7 SOC, Vulnerability Management, Real-time continuous cyber monitoring, Firewall Management, and threat hunting and threat correlation.