Department of Defense (DoD) Supply Chain
The DoD Supply chain (Defense Industrial Base DIB) are under attack
Our nations Department of Defense (DoD) supply chain is made up of over 365,000 suppliers who are mainly commercial entities. "If you are one of the 365,000 DoD suppliers, you are required to have a Cybersecurity program. Your company is probably already under attack all day, every day from nations states trying to extract Defense Information to Bad Actors looking to exploit your data through vulnerabilities, employee training and equipment/software configurations that are insecure.
Challenge
The Cybersecurity Maturity Model Certification (CMMC) framework is designed to protect sensitive unclassified information that is shared by the Department with its contractors and subcontractors and provide assurance that Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) will be protected at a level commensurate with the risk from cybersecurity threats, including Advanced Persistent Threats.
Under the CMMC program, DIB contractors will be required to implement measured cybersecurity protection standards, and, as required, perform self-assessments or obtain third-party certification as a condition of DoD contract award.
Current Schedule and Requirements
- Rule Making scheduled to complete in March 2023
- 90 of 110 requirements implemented for NIST 800-171 is minimum requirement
- All 5 & 3 weighted requirements must be implemented i.e., cannot be on POAM
- 1st contracts, 60 days later, i.e., June 1, 2023
Recent publication:
Current Requirements
All DoD Contractors must meet DFARS 252.204-7012, NIST 800-171 and weighted scores entered into Supplier Performance Risk System (SPRS). The False Claims Act is also being applied for any organization that falsifies information including its cybersecurity posture and scores. The seriousness of these fines or penalties and their impact to a small business could be unrecoverable.
The language around compliance indicates the loss of contracts would still be applicable if a supplier fails to meet compliance or does not have an acceptable continuous improvement plan in place and documented on a Plan of Action and Milestones (PoAM).
Recent publication:
It is recommended to use a 3rd party organization that has experience in assessments under these frameworks and the ability to validate artifacts to support your organization in the case of an audit. In addition to working through the standards, vulnerability management, and continuous monitoring will reduce your likelihood a cyber event notification to the DoD.
)
Solution - CMMC Guidance (2.0)
- Organizations who currently comply with National Institute of Standards and Technology (NIST) Special Publication 800-171 Revision 1 (NIST SP 800-171 R1) are well-positioned to receive their CMMC Level 2 certification from an approved third-party assessor. NIST SP 800-171 R1’s 110 security controls (practices) and 14 control families (domains) form the foundation for Level 3.
- Organizations must account for an additional 21 practices and 3 domains (asset management, recovery, and situational awareness). They also must be able to demonstrate an appropriate level of process maturity to maintain good cyber hygiene (review activities for adherence to policies and practices and provide adequate resources to conduct the reviews and respond accordingly).
- The additional practices – derived from sources including ISO 27001, the Center for Internet Security Controls (ISC), and the Software Engineering Institute’s CERT Resilience Management Model – support capabilities such as CUI labeling and handling, risk assessment and mitigation, network and system monitoring, software code reviews, and email protection.
Cytellix Advantage
Cytellix® has over two decades of experience providing compliance-based cybersecurity for some of the largest networks in the world including the US Army, Intelligence Community and other Federal Agencies. We have observed many companies investing manpower and security tools rather than cost effective solutions with business outcomes. The Cytellix® SaaS platform can you save 75% of a Do-It-Yourself or hiring consultants.
To address cybersecurity outcomes as a business decision, Cytellix® built and delivers a patented turnkey cybersecurity risk management platform rooted in cyber-frameworks.
- Complete view of all cyber compliance, vulnerability, and security events in real time
- Insight into abnormal activities and devices on the network via cyber analytics
- Stronger security and compliance via a complete, centralized network asset inventory
- Streamlined compliance and reporting through automated audit processes
- Accurate and simplified reports with no burden on network or security teams
- Artifact collection and validation automation
- Advanced Monitoring, Response and Vulnerability solution delivered turnkey
- Hierarchical management of organizations, subsidiaries and supply chains
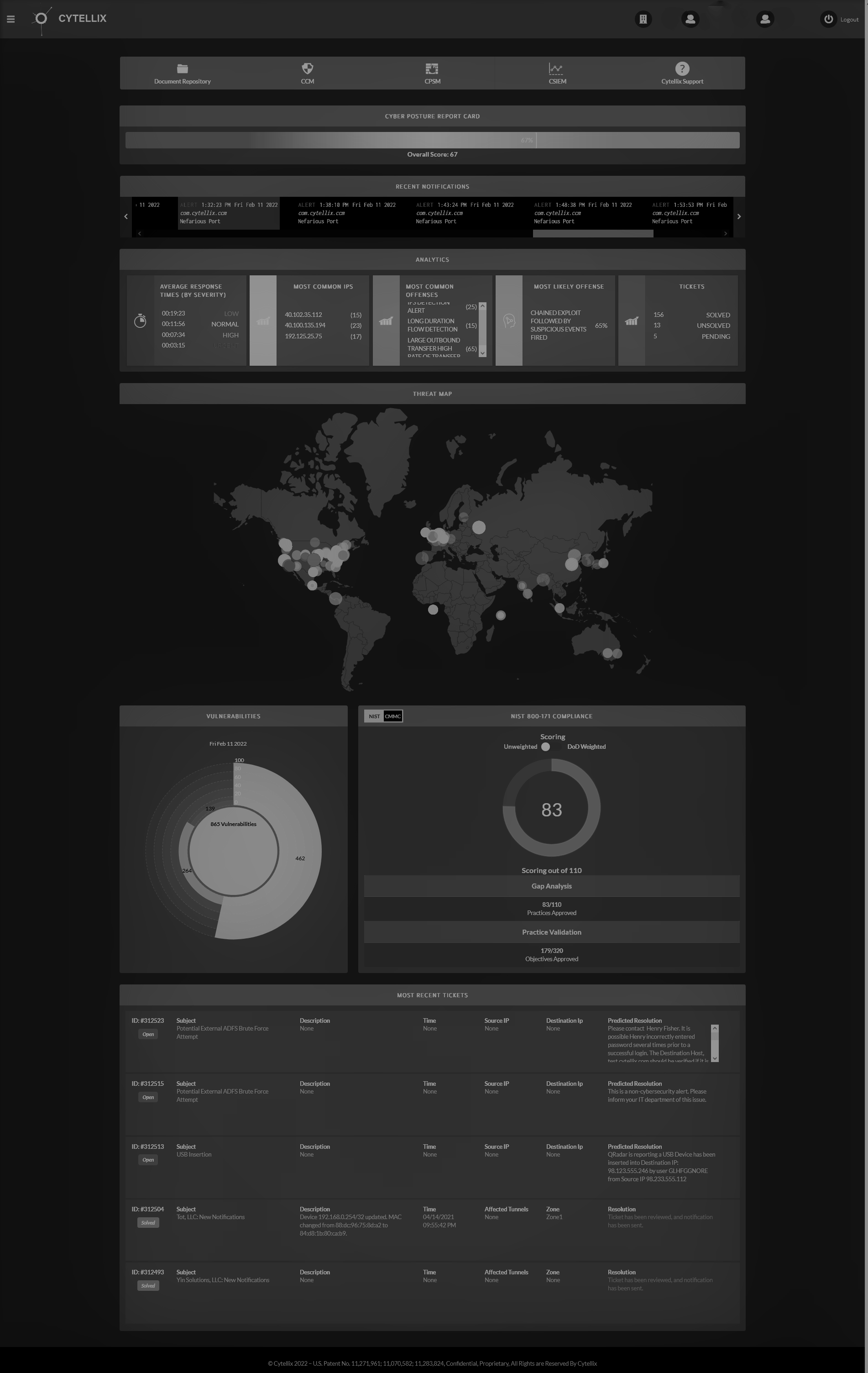
Cytellix® Platform
Let's talk about DFARS, SPRS, NIST, CMMC
Strengthening the security and preparedness of every supplier is vital to our national security as well as economy. To explore how we can assist your organization, and to schedule an a free evaluation of your current cybersecurity posture, contact us.