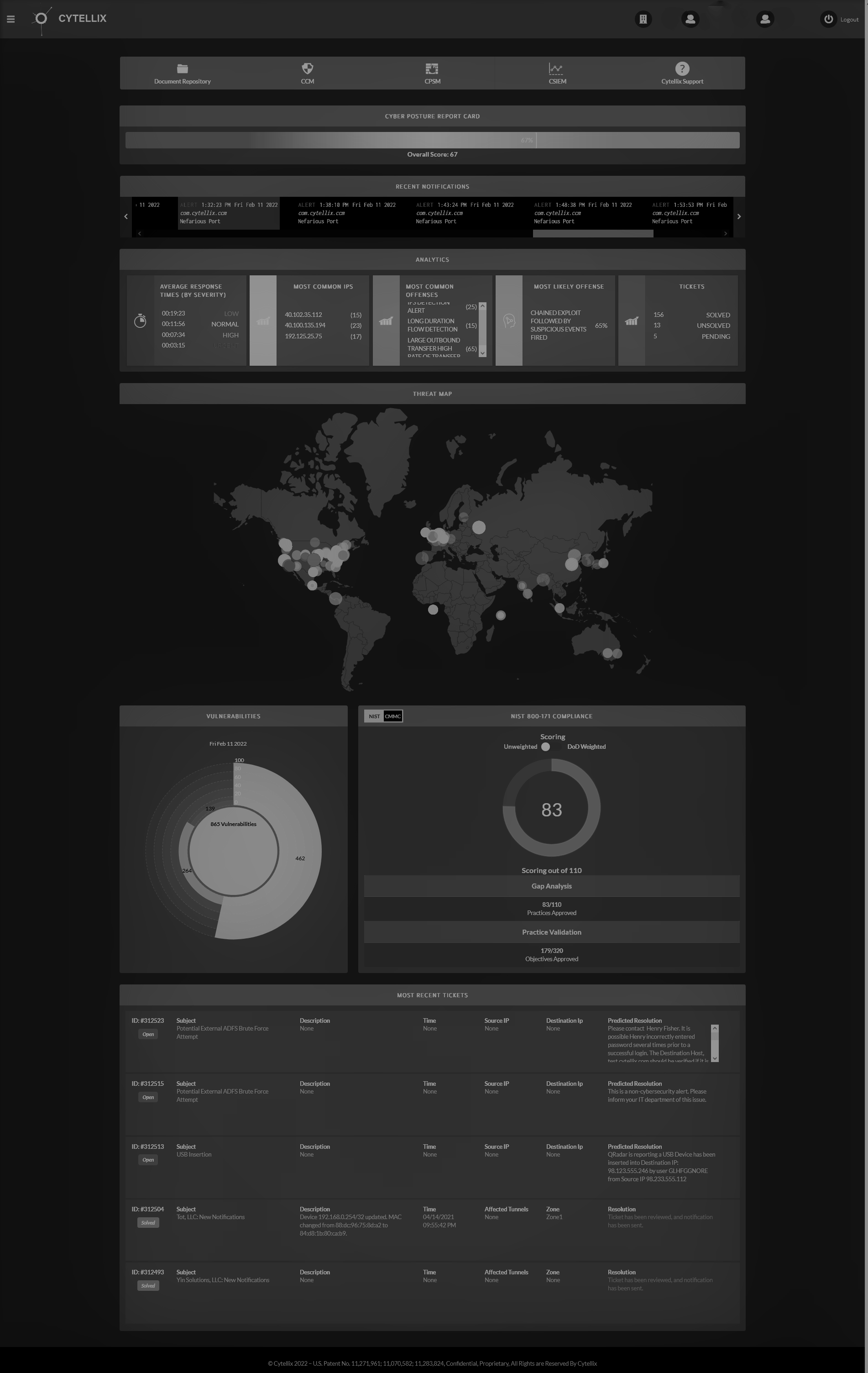
Cytellix® Cyber Watch Portal
(C-CWP™)
“Given the human capital constraints, efficient cybersecurity remains out of reach for the majority of organizations. As such, there is an increased desire to consolidate security products into multifunction solutions addressing a broad set of related challenges, such as securing "hybrid work” or “cloud workloads”" Gartner, Top Trends in Cybersecurity 2022, Author Peter Firstbrook et al, 2/18/22 GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Cybersecurity is a Business Decision
Cybersecurity demand for a more comprehensive, integrated and complete platform is enabling organizations to buy more cost-effective solutions while improving awareness, visibility and response. Cybersecurity standards are driving the consolidation of tools into an intuitive and measured solution.
Solution - Cytellix® Cyber Watch Portal (C-CWP™)
Cytellix® is a first-of-its kind SaaS platform that brings together practical cybersecurity, cyber-compliance, risk management and managed detection response under one umbrella. We know your “real security posture” and can provide a new way to manage and deploy cybersecurity capabilities, risk awareness, and compliance with a plan tailored to your specific situation and needs.
AS AN INITIAL TEST, CONSIDER THESE THREE QUESTIONS:
- Do you have advanced security, cybersecurity and risk management programs in place?
- Is your business prepared in the likely event of a cyber-attack?
- Are you in compliance with your contracts or have regulatory concerns that have a cybersecurity compliance requirement?
If the answer to any of these is “no”, please get in touch and we can provide unbiased guidance.
C-CWP™ at a Glance
Fulfilling Top Trends in Cybersecurity
C-CWP™ provides value by baselining the truth about the true cyber posture of our customers. We then move towards a cybersecurity mesh architecture of integrated continuous improvement that aligns with business objectives. C-CWP is an interoperable and open platform designed for change in posture and threat landscape. C-CWP is delivered as a complete “turnkey” outsourced service or in combination with internal teams and previously purchased security capabilities..
- Reframing the Security Practice C-CWP™ is a cybersecurity framework-based solution that provides real-time awareness, and visibility of your organization’s cyber posture, risks and threats across business units and divisions. C-CWP™ provides one single pane of glass to support the entire organizational needs, views and workflows.
- Rethinking Technology C-CWP™ is rooted in Cyber Compliance standards and leverages patented applications, artificial intelligence, machine learning, automation, telemetry and solutions targeted to the highly regulated industries: DoD Supply Chain, Medical Supply Chain, Pharmaceuticals, Financial Services, Utilities, State/Local Government, Federal Agencies, and any organization requiring Cyber Insurance.
- Responding to Sophisticated New Threats C-CWP™ will reduce overhead costs, improve security awareness, visibility and reaction time compared to other services from MSSP’s, internal resources or combination of the two. Leveraging C-CWP™ as a framework for GRC/XDR/MDR/EDR provides an enhanced cybersecurity standards-based approach to identifying and responding to new and emerging threats.
- Patented
Unique Discovery Capabilities of Cytellix® Cyber Watch Portal (C-CWP™)
Cytellix® Continuous Monitoring (CCM)
Cytellix Continuous Monitoring (CCM) is a Standard in Our GRC, MDR and XDR Solutions
Steady State
Upon initial deployment, a baseline and profiling of normal network behavior is established over a short time period. This baseline describes the network’s steady state, or range of behavior that indicates network health and normalcy. Cytellix® then continuously monitors and flags any departure from one or more parameters as anomalous.
Endpoint & Peremiter Security Management
This enables devices such as PCs, laptops, smartphones, IoT devices and tablets that do not comply with your enterprise and network policy to be rapidly identified. Security management allows you to identify all ingress and egress points on your network, including rogue and unauthorized Internet connectivity.
Permieter Breach Detection
An enterprise-grade, cross-zone leak detection service, not available with any other tool or solution, enables testing for unintended or unauthorized connectivity between your network and others on a completely validated network map.
Progress to Auto-Pilot
As new infrastructure elements are discovered, results are automatically tuned and refined. Discoveries also trigger new threads of collection activity. The raw data backing map nodes is automatically updated, and maps refresh to display newly discovered entities. IT professionals, SOC, and analysts are then alerted only to those network events that merit attention. All of this happens on a continuous, real-time basis.
Reporting, Mapping & Visualization
Discovery results are mapped to a tiered conceptual model that originates in your organization and is understood by its members. Your enterprise receives a broad, comprehensive and navigable representation of its current IT infrastructure. This visual expression of your network serves as an invaluable tool that facilitates communication across disciplines and business units.
Alerts, Warnings & Information
Notifications are sent by the system, by email and text messaging, on occurrences and anomalies that fall outside your company’s policy and parameters. You decide, we enable, which events warrant an alert, and can prioritize the level of urgency associated with each category of event. This feature makes it easier to channel resources and attention to events that matter most.
Network & Device Discovery
Receive visibility of every device, and every connection, on your network, so you have a complete and accurate inventory of all routes and appliances that run on it. Monitoring discovery results on an ongoing basis aids in optimization of system health, and mitigation of risk. The network and device yield becomes even more valuable as a precursor to other discovery methods that reveal other facets of your network ecosystem.
We can also offer key business benefits, such as:
- Business models that scale with demand and functionality
- Reduction in overhead costs
- Improved security by leveraging our real-time cyber platform
- Fast return on investment
- Constant ability to scale and adapt new solutions
- Enhance your cyber awareness with affordable enterprise grade solutions
- Security response capabilities that are customized to meet your expectations
In addition, you’ll have access to our 24x7x365 USA-based Cytellix® Security Operations Center, which offers real-time analysis of latest cybersecurity issues facing commercial, federal, state and small to medium businesses.
Our mission is to protect businesses small and large from cybersecurity threats, not just today but for the future. We keep organizations cyber prepared and compliant with a security framework that combines deep subject matter expertise and patented technology designed to evolve as quickly as threats evolves, preventing attacks before they occur.