Hackers Are Getting More Advanced: Stay One Step Ahead

Individuals and enterprises alike are well aware that technology is almost constantly changing and advancing. We are able to do things today that past generations would have never thought possible! While technology is hugely beneficial to companies, its volatile nature is proving to be problematic at times as well. Businesses need to stay on their toes to adapt to changing software and solutions as quickly as possible. Cybercriminals are busy finding ways to make this more advanced technology a tool for their own use. If you don't stay at least one step ahead, hackers can wreak havoc in your databases. Here are a few tips to stay protected!
Know What You're Fighting Against
The first thing you have to do before you can combat a problem is identifying the problem. You need to know what it is, where it exists, and how serious it is. Cybercriminals are extremely tech-savvy and are well-versed in even the most elite software. Today's online criminals use sophisticated software, bots, viruses, Trojans, and phishing techniques. Unlike hackers of the past, these new-age criminals can automate the entire process; they can be infiltrating your system while they sleep! Passwords are no match for hackers, so you'll need to amp up your cybersecurity game if you want to stand a fighting chance. Once these cybercriminals get in, they don't always steal data these days. Some new attacks now do data manipulation which is far harder to spot than a full-fledged data leak. By changing some numbers here and some addresses there, you could be looking at millions of dollars lost and just as many angry customers. The crimes are getting stealthier, so you need to be more alert than ever.
Continuous Monitoring Is Key
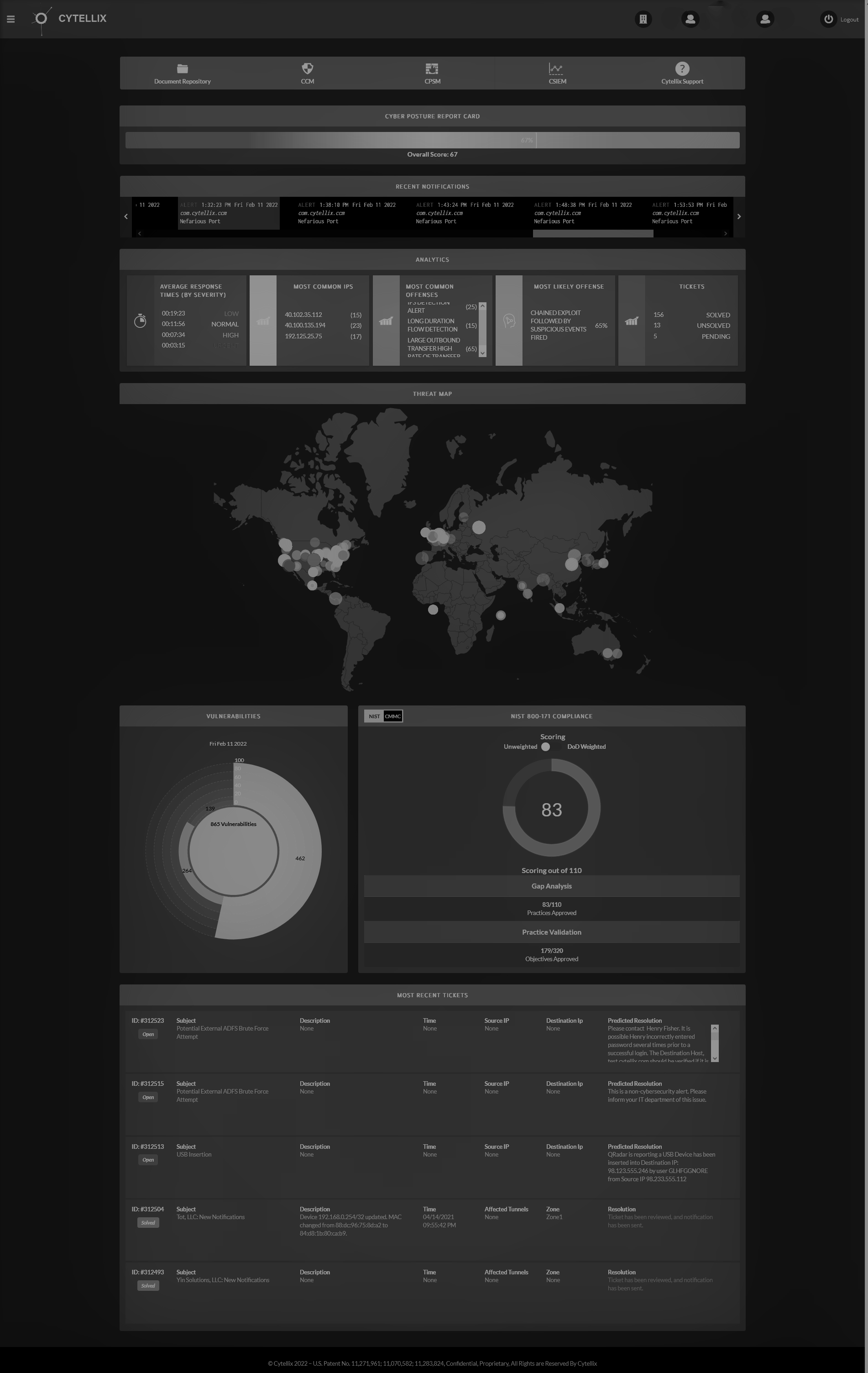
One of the most fool-proof ways of avoiding serious cyberattacks is installing a cybersecurity continuous monitoring system. Your business undoubtedly has many moving parts. If you rely on your employees to keep track of everything, something will eventually fall through the cracks. If you put monitoring in the hands of cybersecurity software leveraging, AI, or other cybersecurity solutions, the odds of missing something important drop exponentially. The Cytellix Cyber Watch Portal (CCWP) puts all the power in your hands. You get a 360-degree view of the inner workings of your company from one convenient platform. With the CCWP, you have constant access to everything that's happening in the company. We can customize the platform to track exactly what you need to stay on top of the game. Our revolutionary technology can even implement solutions on your behalf! When you have a cybersecurity continuous monitoring system, you will be alerted of any abnormal happenings in your systems, networks, and clouds. We understand that cybersecurity requires proactive measures rather than reactive, so our Cyber Watch Portal will let you know if it finds any weakness so that they can be corrected ASAP. We'll be watching 24/7, and hackers won't stand a chance!
Work With A Team Of Experts
Depending on your company’s size, you may find overseeing cybersecurity daunting; problem solved with our easy-to-use Cyber Watch Portal. If cyber seems like an overwhelming concern, or if you simply want to ensure maximum protection against cyberattacks, we highly suggest partnering with a team of experts. Cytellix has been protecting companies big and small for decades. Our technologies grow and change with the cadence of your company and our team adapts accordingly. The Cytellix team can manage your cybersecurity solutions so that you have even less to worry about. We will make updates as necessary based on our findings. We work closely with each client to determine the best course of action when creating a cybersecurity solution package. Our staff is always more than happy to answer questions and provide insight that will improve your understanding of the climate around you. We are just a call away at 1.949.215.8889.
Training Is Essential
Training is absolutely essential when it comes to protecting yourself against cyberattacks. The entire team needs to be trained on technologies to understand the process. You want all data to be entered in the same way in the same place so that it is secure and easy to find. You must train the team on specific processes, technologies, and policies to ensure that everyone in the company is on the same page. Create a very clear hierarchy of access and outline who can access what, when, why, and how. The more uniformly a task is done, the less likely it is to get messed up. Train employees enough that the procedures become second nature. If you rely on certain nomenclature, drill it into the team repeatedly. If you have a strict policy about changing passwords every x-amount of weeks, be sure to follow through if it's not done. You can also consider training the higher-ups to access and interpret the data from the Cyber Watch Portal so that all responsibility is not sitting solely on your shoulders. Our portal is extremely user-friendly and was designed specifically to make your life easier. With the right training, anyone from your team can take the helm and keep watch for problems or security breaks.
It is possible to close the gap between the known and unknown cybersecurity gaps in organizations of any size. We can create custom solutions that bring areas of your company to life that you never looked into before. Our experts will help you identify areas of weakness and will work with you to implement effective and long-lasting solutions. No matter what size your company is, we can help you improve your cybersecurity to protect against hacks. Give us a call at 1.949.215.8889 to speak to our team, or visit
https://cytellix.com/ to learn more about us. We look forward to hearing from you soon!
Cytellix has expert capabilities in cybersecurity technology, risk management frameworks (RMF, NIST, CMMC, GDPR, FFIEC, ISO) and provides a complete visibility platform that supports: DoD customers, DIB Customers, DoD Supply Chain, and other highly regulated industries (Finance, Automotive, Utilities, State and Local Government). Our technology stack includes SIEM as Service, 24x7 SOC, Vulnerability Management, Real-time continuous cyber monitoring, Firewall Management, and threat hunting and threat correlation.
The post Hackers Are Getting More Advanced: Stay One Step Ahead appeared first on Cytellix.