Cyber Hygiene for the New Year

Looking back at 2017 and ahead at 2018, it became clear to me that all the great advice for cyber preparedness is not reaching the small and medium businesses. The questions below were asked of me last week in a presentation in Southern Washington, which prompted me to publish this guidance. Basic hygiene below and a narrative on patching is also included for some holiday reading.
What do I do to protect myself?
1. Have your business cyber assessed
2. Change all your passwords to be unique, do not repeat the same password.
3. Use complex passwords or a password generator
4. Set up monitoring and alerts of banking accounts for money movement
5. Run modern device anti-virus/anti-malware products on all owned devices
6. Make sure you have you don’t have firewall settings at default and use a next generation firewall.
7. Make sure all connected devices are protected and not set to default, segment your data away from IoT devices.
8. Learn about phishing and ransomware best practices
9. Don't surf unknown web sites
10. If mail looks suspicious or your questioning authenticity- investigate
Patching narrative
The issue of deployment of patches or updates by companies is the biggest concern given the public awareness of these broad based cyber/malware attacks. Over the past couple months, the attacks have been based upon the gaps in the “patching” of software or device vulnerabilities. These attackers develop their attacks to automatically detect and exploit these unpatched software or systems that are not updated with the current patch level as the basis for the attack and entrance to a company.
When a device manufacturer such as a network switch, firewall or router is identified as “end of life” EOL, then it either has a technological market disadvantage or a technical flaw that renders the device vulnerable in certain situations. The manufacturer does two things very well: One, they market the advantages of the next new device with all the capabilities and features that are compelling to “buy” or “upgrade”. Secondly, they publicly identify the flaws and gaps and or vulnerabilities with the strongly urged recommendation to upgrade to the new product to occur. This is normal course of business and does provide full disclosure to their customers.
The other side of this coin, is the same publicly known data used to communicate gaps and flaws is used to create distributed attacks on targeted devices. Once a flaw is known, the hacker communities are also aware and start their targeted attacks to enter an organization through the identified flaws. Yes, we are doing a great job telling the hacker communities how to hack. Call it the unintentional, borderline intentional published hack advisory!
Software patches are similar in respect but much more frequent. Microsoft, Google, WordPress, Apple, Adobe as examples typically call the patches security updates or security bulletins. Many of the updates are categorized as Critical, Important or Moderate. They also identify the issue either part of the native vendor products or vulnerabilities in 3rd party applications used by the native applications that can compromise the OEM publisher’s products. The OEM publishers have a significant role to play and this is not trivial work. To be fair, the OEM’s are not intentionally building vulnerable products, they find vulnerabilities over-time in either their native code or 3rd party licensed code and as a system require an update or patch. In addition, each patch update could in theory also inject new unknown flaws, fix one and then start another.
Why don’t companies patch? Process and procedures say wait? Resources are unavailable? Other projects have priorities? Will the patch break proprietary software/systems that run the business? Knowledge of all available patches? Frequency of patches? Likely some or all of these apply to someone you know. Is it worth it? Given what we know about the magnitude of the impact of these recent attacks, why are you waiting to patch?
Proper cyber hygiene could save your company and job!


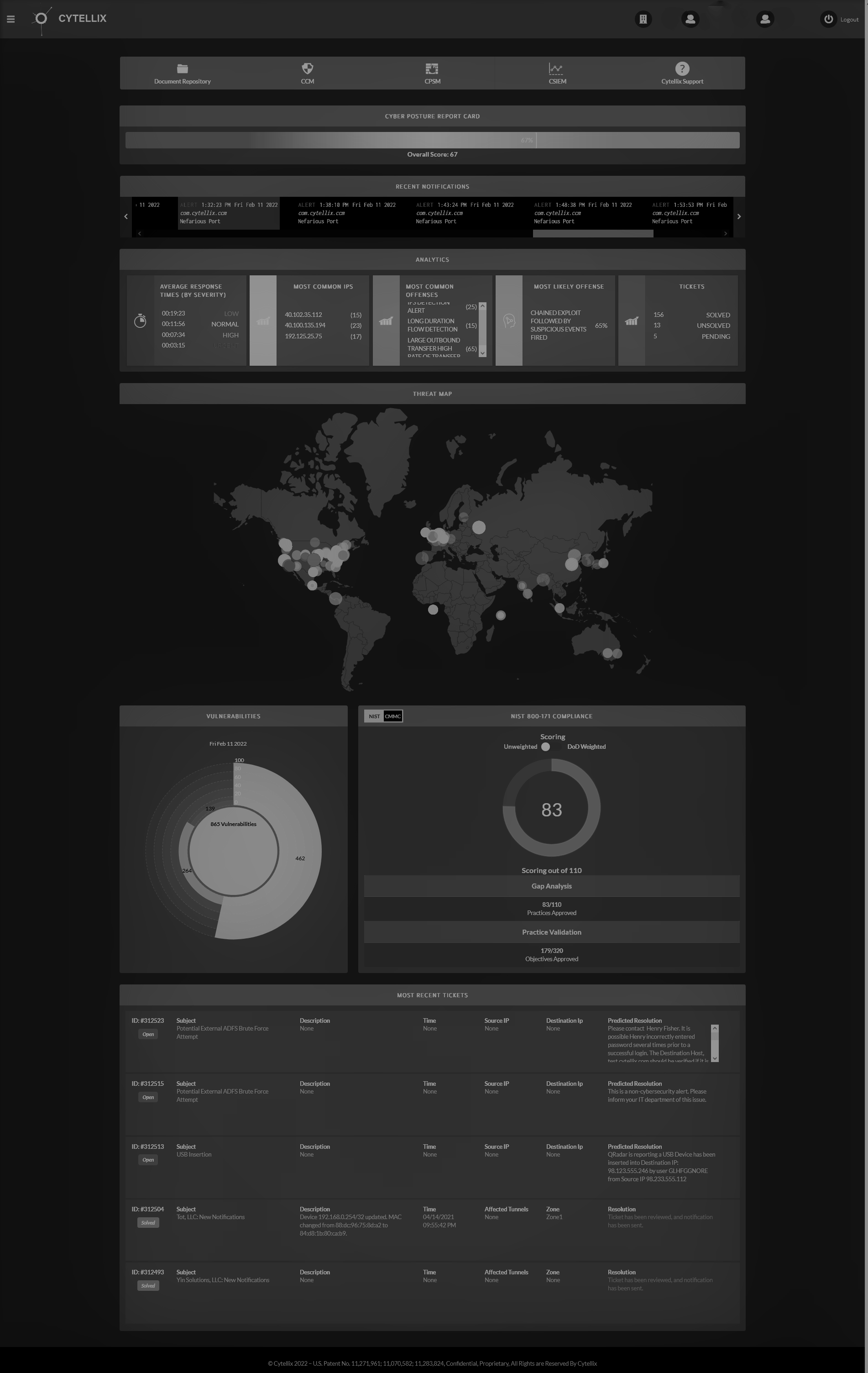
Cytellix® Cyber Watch Platform (C-CWP™)
C-CWP™ provides value by baselining the truth about the true cyber posture of our customers. We then move towards a cybersecurity mesh architecture of integrated continuous improvement that aligns with business objectives. C-CWP™ is an interoperable and open platform designed for change in posture and threat landscape. C-CWP™ is delivered as a complete “turnkey” outsourced service or in combination with internal teams and previously purchased security capabilities

Cytellix® Endpoint Detection Response (C-EDR™)
Cytellix® Endpoint Detection & Response (C-EDR™) is a flexible solution that can be used standalone, enables bring-your-own-license or can be provided turnkey as a complete managed solution with our C-GRC™, C-MDR™, XDR, SOC 24x7x365 managed Turnkey Solutions. The Cytellix turnkey C-EDR™ is a Enterprise grade solution that is complete and has full integration with the Cytellix platform.

Cytellix® Governance Risk & Compliance (C-GRC™) & IT Risk Management (IRM)
Risk Management requirements are evolving to align to the changes arising from compliance risk shifting towards regulatory impact on business process. The demand on organizations to understand their cybersecurity posture, report status and meet regulatory obligations is driving demand across the enterprise (small>large) for a non-technical, turnkey all-inclusive platform.

Cytellix® Managed Detection Response (C-MDR™)
Patented technology compiles information from the vulnerability's, governance, risk, compliance assessments, event data, and analytics. Delivers real-time analysis, including continuous improvement visualization and scorecard.

Extended Detection Response (C-XDR™)
The Cytellix® Extended Detection Response (C-XDR™) solution leverages our flagship Cytellix Cyber Watch Portal (C-CWP™) as turnkey compliance, awareness and response platform. Our C-XDR™ includes, vulnerability management, devices profiling, network segmentation, asset discover, threat intelligence, leak detection, EDR, pre-defined use cases for log ingestion and correlation of threats and our USA based 24x7x365 Security Operations Center (SOC). The Cytellix platform leverages our in-house AI/ML models for real-time telemetry, threat discovery/hunting and ticket reduction. This is a complete turn-key, affordable XDR solution.

Cybersecurity for Small and Medium Business
Cytellix® has designed its platform to enable the small and medium business to adopt quickly, with low friction at an affordable price. We have found that the tasks of both regulatory compliance with cybersecurity frameworks and building a high quality cybersecurity monitoring and infrastructure is a significant time, resource and expense issue for SMB's.
How We're Different
Cytellix® is a first-of-its kind patented SaaS platform that brings together cybersecurity, compliance, and risk management under one fully integrated umbrella. We know your "real security posture" and can provide a new way to manage and deploy cybersecurity capabilities, risk awareness, and compliance with a plan tailored to your specific situation and needs.
Contact Us
- ssdfsThank yo for subscribing.
We will get btackts to you as soon as posTsible.
Oops, there was an error sending your message.
Please try again later.
The Cytellix® team of experts have been delivering cybersecurity for the past 15-years to some of the largest networks in the world. This expertise is delivered to our SMB customers as an affordable, precise, and comprehensive solution designed for organizations who need to comply with Cybersecurity regulatory requirements. There is no other fully integrated GRC, MDR, XDR, EDR single pane of glass solution that is as rich in capabilities, as easy to use and available in production today.
General Inquiries: 1.949.215.8889
Cytellix® - Patent Pending. All Rights are Reserved By Cytellix®




