Artificial Intelligence (AI) Cybersecurity: It’s All About Behavior!

The latest leading-edge data intelligence topics referred to as Artificial Intelligence (AI), Machine Learning (ML) and, Artificial Neural Networks (ANN) are currently experiencing significant venture and corporate capital investments. Some of the advantages of ingesting large quantities of data and creating a corpus of knowledge to draw insights are very interesting for complex subjects such as cybersecurity, healthcare and financial services. The use cases of AI in healthcare such as DNA/genome research are truly captivating to read. The parallels to cybersecurity research and respective knowledge base for predicting and analyzing data will be step-functions of change needed to understand the data collection and interpretation of threats. The application of any form of AI includes a “people factor,” as directly linked to both ends of a “cyber activity.” A “cyber event” is started by a person and the resolution is implemented and managed by the same.
The behavior part of cybersecurity also involves people, but machine behavior plays a significant role in cyber events. For example, if we can measure a baseline of machine behavior that is “known good,” then we can react—potentially in real-time—to machine changes in behavior. There are many parameters to consider and behaviors that may be considered non-issues to filter; however, having a system of behavioral analytics under the category of AI/ML/ANN brings data-driven decision making.
A few scenarios to outline this include known devices on the network or IoT devices changing their state. In the first case of known devices, this has been a topic we have been discussing in the security space for a very long time. Products and technologies have been built for attestation, key management and device authentication—to capture a few categories. As we move up a level from the cryptography space to understanding the metadata a device produces, we can measure changes, arrival, departure and state. By observing anything with an IP address in relationship to the context of its metadata, we can filter “good” and “bad” activities, behaviors and changes. If a known device comes on the network at 8 am on Monday normally, but an unknown device comes on the network at 3:00 am, we can create an action to change that behavior and thus become proactive in our cyber preparedness. Alternately, if a known device that was once considered “good” starts talking to a “bad” actor site or shows a change in its metadata that is considered out of policy/standard, then actions can be taken to quarantine or remediate accordingly.
In the second example of IoT devices changing their state, we have seen this with IP cameras, and medical devices. The potential case of industrial systems being taken over by the “zombie robot apocalypse” is not as far removed from reality as one might think. Hackers can exploit flaws and create subtle changes to industrial control systems, which could be dramatic in scale or event. I am not suggesting that the machines will take over the world, but I am suggesting close monitoring of IoT devices for behavioral changes that could indicate the presence or possibility of a wider scale issue.
As an industry, we can start to move from a reactive to a proactive state in the category of cyber preparedness. A real-time approach to monitoring device behaviors could reduce cyber event time to discovery from the current industry average of 256 days. The cost of discovery time is escalating every year. Our small and-medium businesses cannot afford the costs of remediation and losses that accompany a cyber event. The statistics of survival for SMBs in a cyber event estimate that roughly 60 percent or 6 out 10 will not be in business in six months.
The current state of cybersecurity necessitates the establishment of continuous monitoring practices—to monitor both known devices on networks and IoT devices changing their state. The innovations of artificial intelligence (AI), machine learning (ML) and artificial neural networks (ANN) are paving the way for a proactive cyber approach.


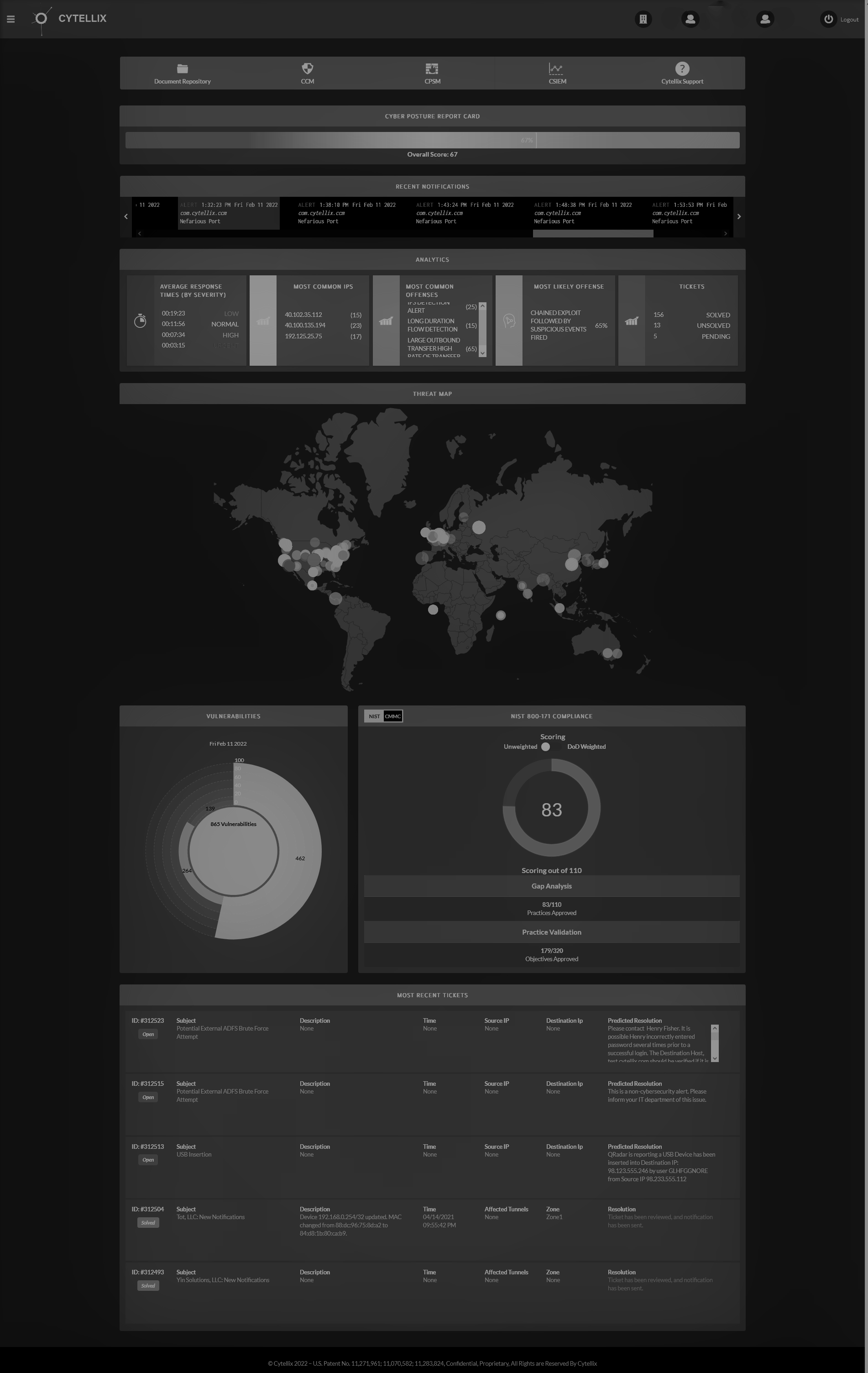
Cytellix® Cyber Watch Platform (C-CWP™)
C-CWP™ provides value by baselining the truth about the true cyber posture of our customers. We then move towards a cybersecurity mesh architecture of integrated continuous improvement that aligns with business objectives. C-CWP™ is an interoperable and open platform designed for change in posture and threat landscape. C-CWP™ is delivered as a complete “turnkey” outsourced service or in combination with internal teams and previously purchased security capabilities

Cytellix® Endpoint Detection Response (C-EDR™)
Cytellix® Endpoint Detection & Response (C-EDR™) is a flexible solution that can be used standalone, enables bring-your-own-license or can be provided turnkey as a complete managed solution with our C-GRC™, C-MDR™, XDR, SOC 24x7x365 managed Turnkey Solutions. The Cytellix turnkey C-EDR™ is a Enterprise grade solution that is complete and has full integration with the Cytellix platform.

Cytellix® Governance Risk & Compliance (C-GRC™) & IT Risk Management (IRM)
Risk Management requirements are evolving to align to the changes arising from compliance risk shifting towards regulatory impact on business process. The demand on organizations to understand their cybersecurity posture, report status and meet regulatory obligations is driving demand across the enterprise (small>large) for a non-technical, turnkey all-inclusive platform.

Cytellix® Managed Detection Response (C-MDR™)
Patented technology compiles information from the vulnerability's, governance, risk, compliance assessments, event data, and analytics. Delivers real-time analysis, including continuous improvement visualization and scorecard.

Extended Detection Response (C-XDR™)
The Cytellix® Extended Detection Response (C-XDR™) solution leverages our flagship Cytellix Cyber Watch Portal (C-CWP™) as turnkey compliance, awareness and response platform. Our C-XDR™ includes, vulnerability management, devices profiling, network segmentation, asset discover, threat intelligence, leak detection, EDR, pre-defined use cases for log ingestion and correlation of threats and our USA based 24x7x365 Security Operations Center (SOC). The Cytellix platform leverages our in-house AI/ML models for real-time telemetry, threat discovery/hunting and ticket reduction. This is a complete turn-key, affordable XDR solution.

Cybersecurity for Small and Medium Business
Cytellix® has designed its platform to enable the small and medium business to adopt quickly, with low friction at an affordable price. We have found that the tasks of both regulatory compliance with cybersecurity frameworks and building a high quality cybersecurity monitoring and infrastructure is a significant time, resource and expense issue for SMB's.
How We're Different
Cytellix® is a first-of-its kind patented SaaS platform that brings together cybersecurity, compliance, and risk management under one fully integrated umbrella. We know your "real security posture" and can provide a new way to manage and deploy cybersecurity capabilities, risk awareness, and compliance with a plan tailored to your specific situation and needs.
Contact Us
- ssdfsThank yo for subscribing.
We will get btackts to you as soon as posTsible.
Oops, there was an error sending your message.
Please try again later.
The Cytellix® team of experts have been delivering cybersecurity for the past 15-years to some of the largest networks in the world. This expertise is delivered to our SMB customers as an affordable, precise, and comprehensive solution designed for organizations who need to comply with Cybersecurity regulatory requirements. There is no other fully integrated GRC, MDR, XDR, EDR single pane of glass solution that is as rich in capabilities, as easy to use and available in production today.
General Inquiries: 1.949.215.8889
Cytellix® - Patent Pending. All Rights are Reserved By Cytellix®




